Hyper-V 2012 and 2012 R2 live virtual machine memory acquisition and analysis
Monday, 28. April 2014
Introduction
In my previous post I went over analyzing Hyper-V saved state files in Volatility using a tool call vm2dmp. I mentioned some limits of the tool for VM’s on 2012 and later Hyper-V host systems. Another major downside was a limit of 4GB RAM size on the VM, which would cause the tool itself to crash out. However the biggest downside was having to actually pause a running VM to obtain the data with no live acquisition option for anyone who can’t just take a server down in the middle of the day.
Using a tool called LiveKd we now can analyze Windows virtual machines on both the 2012 and 2012 R2 platforms including VM’s with RAM sizes larger than 4GB. LiveKd also brings a major feature that vm2dmp wasn’t capable of, you can use it to dump out the memory of a live VM into Microsoft crash dump format without pausing it. This will be very critical for an incident response analyst that can’t pause VM’s for memory acquisition. LiveKdalso requires that the Debugging Tools for windows be installed on the Hyper-V host itself which can have some impact if you don’t already have them installed.
Acquisition
Requirements for the Hyper-V host
Install the Debugging Tools for Windows
Download LiveKd from Sysinternals and extract to the directory of C:\Program Files (x86)\Windows Kits\8.1\Debuggers\x64
Run an elevated command prompt and change the directory to the location of LiveKd.exe
Run livekd.exe (Accept the EULA)
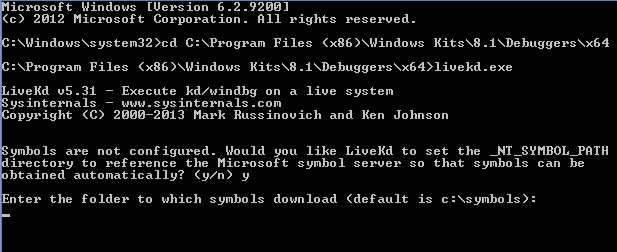
If you haven’t installed symbols for the Hyper-V host, LiveKD will ask if you want it to automatically configure the system to use Microsoft’s symbol server, or you can manually set the symbols yourself.
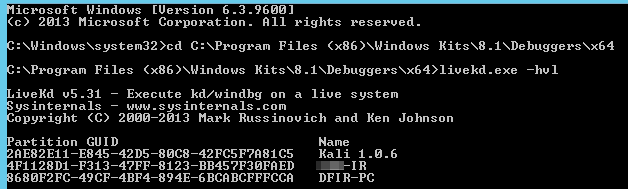
If you want to list the virtual machines on the server just use the –hvl options and it will list GUIDs and names of running Hyper-V VM’s.
Example: livekd.exe –hvl
If you want to create a full crash dump of a virtual machine running on the host system you would run
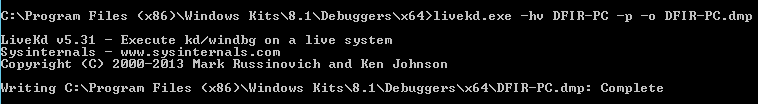
>livekd.exe –hv (System name or GUID) –p (to pause the system to create a more consistent image) –o (output-file)
Example: livekd.exe –hv DFIR-PC –p –o DFIR-PC.dmp
If the virtual machine cannot be paused due to business reasons, you may omit the –p command line option, and create a crash dump from the live running VM. From my testing I can confirm that very little image smearing occurs. For further command line options visit Using LiveKD. Because Volatility supports the crash dump address space you can then use all the normal plugins.
Once you have converted to a crash dump you then use Volatility’s Imagecopy plugin to convert the crash dump format to a raw memory dump.
Example: python vol.py –f /dir/crash dump
–profile=/profile/of/vm/ -O /dir/memory.raw
Once the memory dump is in a raw format you can use the raw image in other tools like Redline.
Currently this process is limited to virtual machines running Windows only, in my next blog post I’ll discuss the acquisition process for linux VM’s in Hyper-V 2012 R2.
If anyone has any helpful feedback please DM me on twitter @wyattroersma even more so if you have found something stated here that isn’t accurate.
Other References:
http://blogs.technet.com/b/markrussinovich/archive/2010/10/14/3360991.aspx