HYPER-V MEMORY FORENSICS PLUGINS WITH VOLATILITY
Friday, 17. October 2014
My motivation for this project has to do with the number of hyper-v systems that I interact with on a day-to-day basis. I recently came across a compromised Windows 2008R2 Hyper-V host and wrote this plugin to improve my understanding of the code base and to create something useful for future use. Hopefully there is some interest in the plugin so I can continue its development to enhance its features.
Anyone looking for the GrrCON 2014 presentation you can get it here https://drive.google.com/file/d/0Bz3L4ZnVlUY8RlNsR1FpY0o5V1U/view?usp=sharing
I have three very simple, but useful plugins currently, which are hpv_vmconnect, hpv_vmwp, and hpv_clipboard. You can download them at: https://github.com/wroersma/volplugins/blob/master/hpv.py
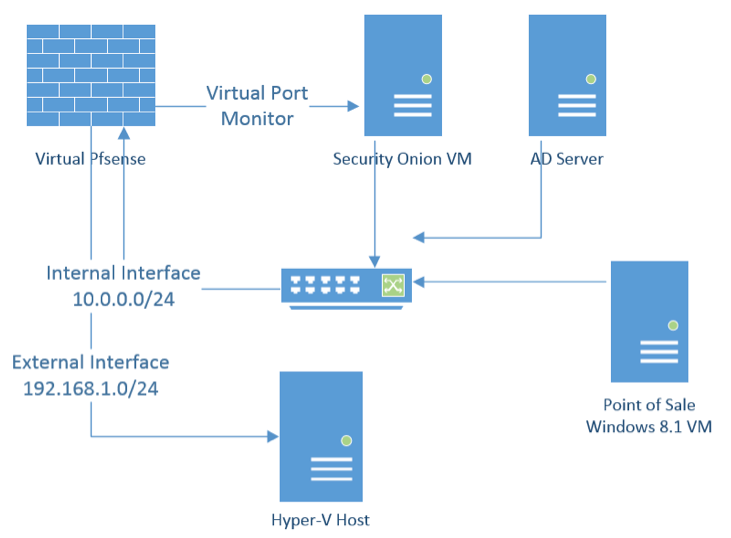
To help you visualize how the networking is configured on my hyper-v host, here is a simple Visio diagram of how it’s set up.
hpv_vmconnect
The vmconnect plugin tells you what user is currently using the virtual connect console on a particular virtual machine. It displays their username, the domain they are connected from, and the create time also reflects when the current console was last accessed.
~/python vol.py -f Win2012R2.vmem –profile=Win2012R2x64 hpv_vmconnect
Volatility Foundation Volatility Framework 2.4
Process: vmconnect.exe
PPID: 1552
PID: 2684
Create Time: 2014-09-28 05:12:54 UTC+0000
Host Computer Name: HV01
User Name: wyatt
User Domain Name: domain.local
VM GUID: 16AA09F1-2B2C-4B8E-A46E-E6FAD7988878
hpv_vmwp
The virtual machine GUID is the biggest identifier of the virtual machine and its components. A user account with the GUID is dedicated to this process and has no rights otherwise. Using the GUID you can identify which process is running for each virtual machine on the hyper-v host server. More information can be found manually and I’d like to expand the plugin at some point to support that as well. The create time does reflect when the last virtual machine was started.
My original goal for this plugin was to implement a memory mapping technique from this process to the virtual machine. Unfortunately I was unable to accomplish this in time due to my lack of understanding, but will hopefully have time to finish this up in the near future.
~/python vol.py -f Win2012R2.vmem –profile=Win2012R2x64 hpv_vmwp
Volatility Foundation Volatility Framework 2.4
Name PID PPID Create Time GUID
—————- —— —— —————————— —————————————-
vmwp.exe 2684 1552 2014-09-28 05:10:37 UTC+0000 16AA09F1-2B2C-4B8E-A46E-E6FAD7988878
hpv_clipboard
While I need to improve upon the formatting, this plugin displays data typed the hyper-v virtual console through the “Type Clipboard Text” option and will also display hotkey commands like Ctrl-Alt-Del and if it completed successfully or not.
All clipboard data is listed right after the process in which the data is discovered. I need to work on a better format to display the difference between what each process is responsible for.
~/python vol.py -f Win2012R2.vmem –profile=Win2012R2x64 hpv_clipboard
Volatility Foundation Volatility Framework 2.4
Process : vmconnect.exe PID : 2684
Clipboard Data: Simulating typing Ctrl-Alt-Del.
Clipboard Data: Simulating typing Ctrl-Alt-Del completed successfully.
Clipboard Data: Simulating typing ASCII characters ‘{0}’.
Clipboard Data: Simulating typing ASCII characters completed successfully.
Clipboard Data: Simulating typing ASCII characters ‘d=bp=$6XZ\\ ,
Clipboard Data: Simulating typing ASCII characters ‘d=bp=$6XZ\\ ,y/_}K()Nk!’DVe,
Clipboard Data: Simulating typing ASCII characters ‘d=bp=$6XZ\\ ,
Clipboard Data: Simulating typing ASCII characters ‘d=bp=$6XZ\\ ,y/_}K()Nk!’DVe,
Clipboard Data: Simulating typing ASCII characters ‘d=bp=$6XZ\\ ,y/_}K()Nk!’DVe,
Clipboard Data: Simulating typing ASCII characters ‘d=bp=$6XZ\\ ,y/_}K()Nk!’DVe,
I plan to release another blog post following more data that I’m still in the process of researching. I will also be updating the plugins after some heavy testing, implementing some new features like listing the vm name, IP address, and other information. Follow my twitter account@wyattroersma to receive the latest updates for my blog! Also please feel free to leave feedback or contact me.