Data Recovery DC3 2011 Challenge 303
Thursday, 12. April 2012
I felt like actually putting something out on a website I took down months ago. I have been busy with life crap, school and work. I am here to bring the return of my blog with a little guide or Methodology if you will of a DC3 challenge I did last year for 2011. If you are unfamiliar with the challenge what are you waiting for, a sign? well here is your Link http://dc3.mil/challenge/2012/
To get things into perspective of what the investigation indicated here is the Challenge instructions:
“Description: Examiners must develop and document a methodology used to examine and recover the contents of unallocated media.
The media in this instance is an image of unallocated space from a USB thumb drive. Points will be awarded for recovering files from the image of that unallocated space and for providing the file(s) and any information on the recovered data.
Points will be awarded for the accomplishment in locating and providing the information requested, and the degree that you successfully accomplish this task.
Examiners must also be concerned with recording a detailed methodology of the steps and recording the tools used to accomplish the task as part of their grade.”
That basically cover what they instructed me to do. It also came with a raw image file “Memorex-TD-Classic.dd”
So for those looking for the quick results here they are in a CSV – Report file Files.cvs (Filelist )
If you care about how I got there well I’m getting there.
Frist a reference of all the things others created in order for a Noob like me to be able to pull something like this off.
Methodology
Notes:
Commands are highlighted in Bold Font
Selections are highlighted with Italic Text
The first thought I had was to export the file from the packed rar file they provided us to download. It also came with a provided MD5 Hash so I checked that to make sure it was the right file. (If you don’t know how to file hash I will be posting a how to later, hopefully most reading at least know this much)
I also try to use free programs for the most part however its sometimes has a place to actually use something that costs a little bit of coin.
For the Analysis my first instinct was to open the file in a hex editor and start poking around for information regarding the goodies we can use to recover it with as little effort as possible.
Hex Editor Analysis
I first started by renaming the provided file for process functionality from Memorex TD Classic to Memorex-TD-Classic which helps avoid space errors in some programs. I also created the folder named “303” on the root of my C: drive. I then saved the new Memorex-TD-Classic in directory C:\303\Files.
I then open the file in Hexeditor Version 1.7.7.0 and examined the file and the first important evidence I came across was at offset: 0x00001803 hex value 45 58 46 41 54 which is “EXFAT” in ANSI which indicates a EXFAT file system used to be present on this image.
Understanding that exFAT file systems contain a boot sector for recovery purposes I decided to try and see if I could recover the entire image by restoring the boot sector so the computer could recognize the device. I mean why it would not be this easy to begin with.
I know of a nice little awesome program called testdisk that would easily allow me to pull this off if the recovery boot sector will work. (Note you can manually sure for the header of the boot record but I already knew it was there through my first trial solution that didn’t work)
Testdisk
A testdisk-6.12 program created by Christophe GRENIER has the ability to recover these types of file systems.
Step 1 in testdisk:
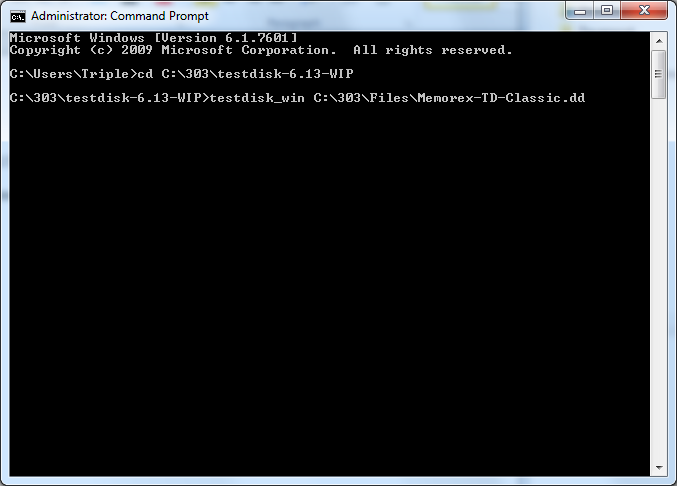
I placed this program into C:\303\ testdisk-6.13-WIP directory for organizational reasons. I opened (with administrative privileges) the command prompt (cmd.exe) and ran the following commands.
C:\Users\Triple>cd C:\303\testdisk-6.13-WIP
C:\303\testdisk-6.13-WIP>testdisk_win C:\303\Files\Memorex-TD-Classic.dd
(Screen shot of step 1 commands)
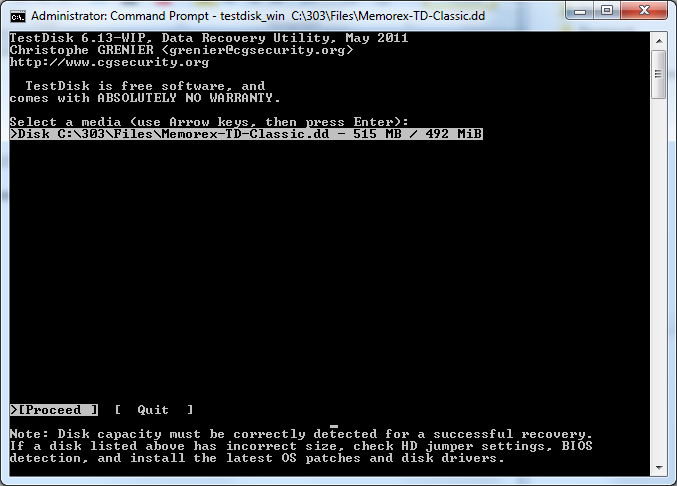
Step 2: Select a media type
I then selected >Disk C:\303\testdisk-6.13-WIP>testdisk_win C:\303\Files\Memorex-TD-Classic.dd -515MB /492 MiB
(Screenshot Step 2 in testdisk: Select a media type)
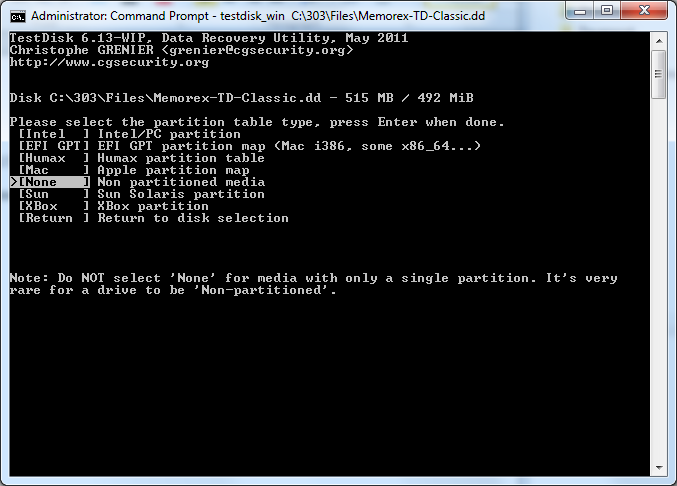
Step 3: Please select the partition table type, press Enter when done
I selected the >[ None ] Non partitioned media because the structure is not any of the other listed formats and also a corrupted format.
(Step 3: Please select the partition table type, press Enter when done)
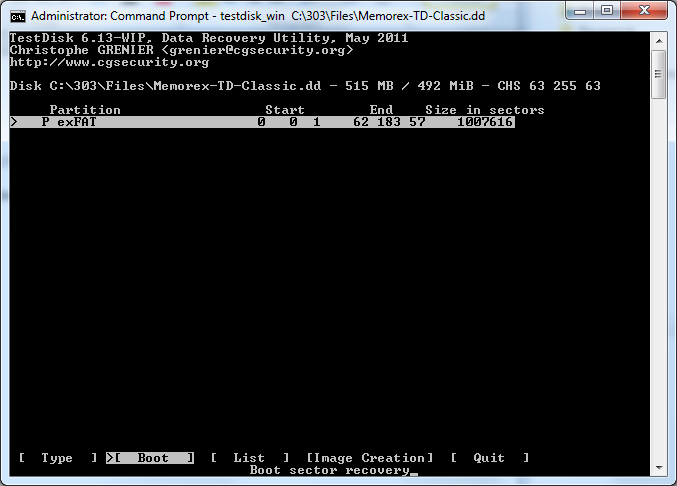
Step 4: Boot Sector Recovery
I then selcted the >[ boot ] Boot sector recovery option on the currently selected file Memorex-TD-Classic.dd.
(Screenshot Step 4: Boot Sector Recovery)
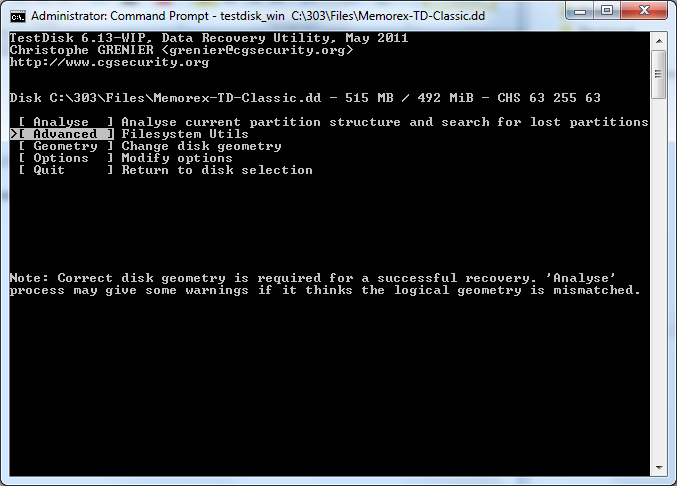
Step 5: Advanced File system Utility’s
I then selected >[ Advanced ] Filesystem Utils
(Screenshot Step 5: Advanced File system Utility’s )
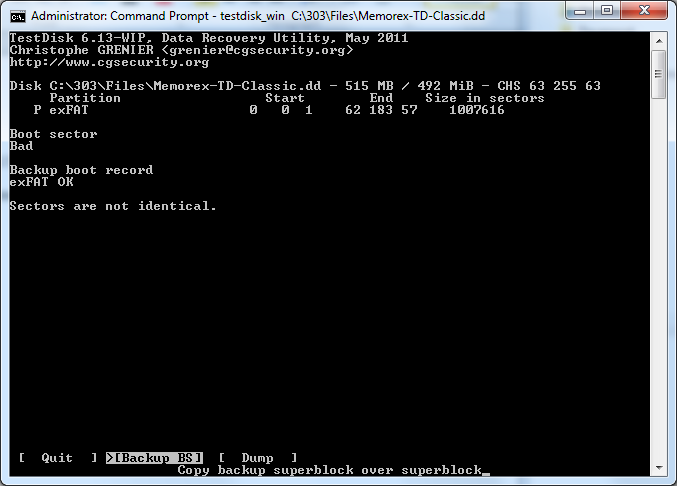
Step 6: Copy backup superblock over superblock
Because the backup boot record is “exFAT OK” there is a boot sector backup that can be written to the main boot sector in order to restore the data in case the main boot record is damaged.
I then selected >[ Backup BS ] Copy backup superblock over superblock
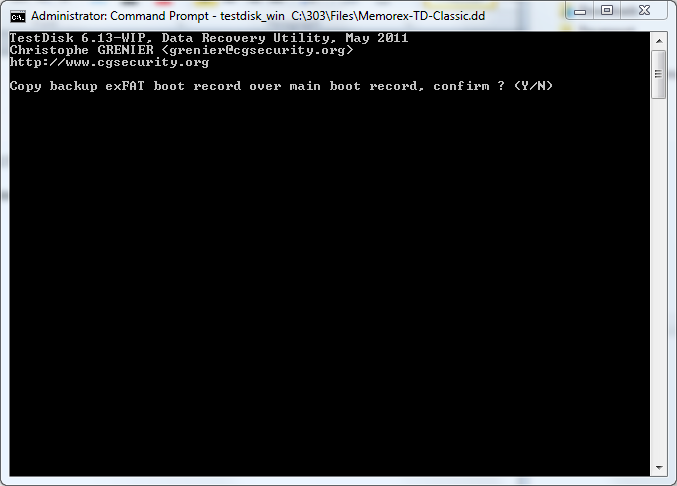
Step 7: Copy backup exFAT boot record over main boot record, confirm? (Y/N)
Confirm the option to right the backup in order to recover the image
***Warning this will write to Evidence file
Type Y >Enter to confirm (Screenshot Confirmation screen)
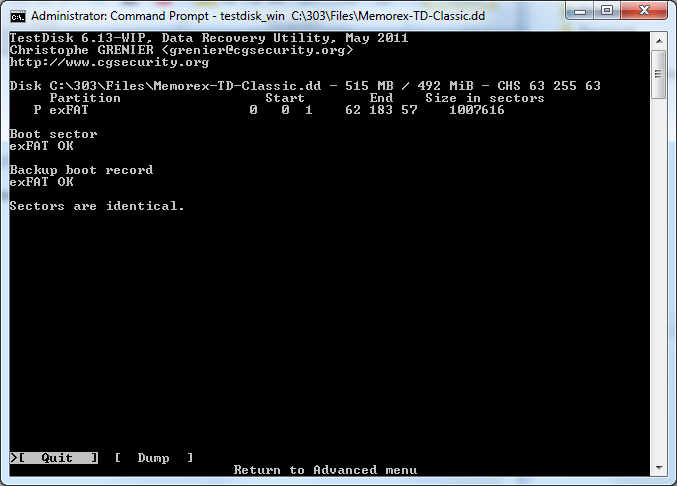
Exit testdisk
FTK Imager
I then turned to AccessData product FTK Imager v3.0.1.1467 in order to mount the recovered image and export the file system in order to ensure the recovery worked.
Adding the image file C:\303\Files\Memorex-TD-Classic.dd
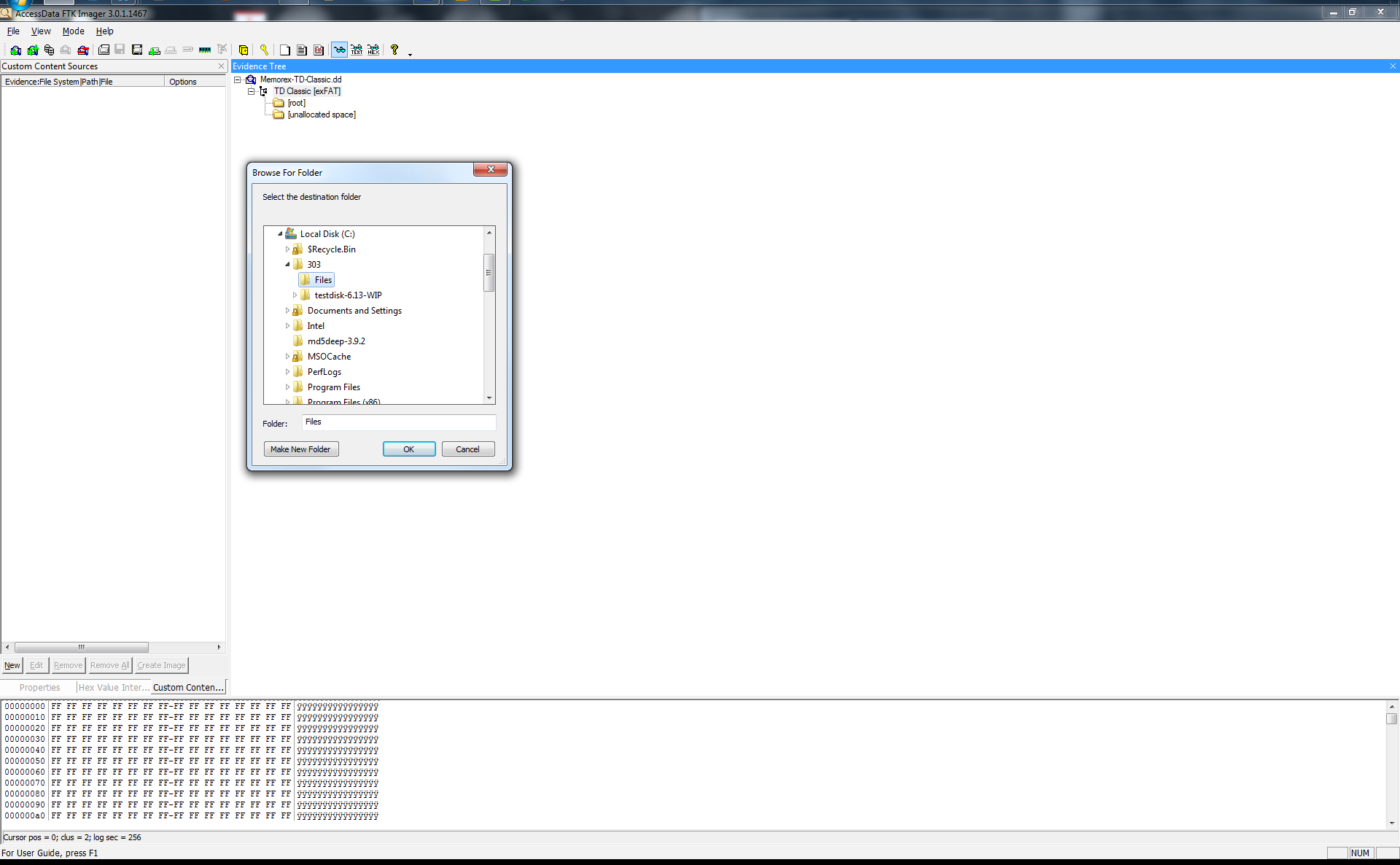
I then selected and right clicked the TD Classic [exFAT] to export a file hash list to C:\303\Files\Filelist.csv
I then selected the TD Classic [exFAT] to export a files… to C:\303\Files\ Memorex-TD-Classic this is evidence files exported from the image file showing that the image is intact after a unallocated file recovery.
You can review the Exported CSV I provided earlier but that is about it and all it took to perform a nice littler repair on some data. If anyone seen anything I missed/did wrong/ could do better please leave a comment and I will be sure to make a note of it and update the guide if need be. A few quick shout outs before I sign off into other random project I do.
I used Evernote for the documentation process and taking the screenshots. http://www.evernote.com/ if you haven’t installed it yet go ahead and give it a try, more than likely you will love it as well.
Also a quick shout out to Mark McKinnon, Andrew Case, and the others that helped me figure challenges out. The forensics community is amazing and extremely helpful when you reach out for it.
Later I’m out.