Wednesday, 2. May 2012
I want to review some notes from another previous Digital Forensics challenge. I will not present anything in here that no one hasn’t seen somewhere else and this is NOT A REAL FORENSICS investigation and nor am I a real forensics expert or professional. I’m a student learning providing some of the very little I know.
I am only putting up notes if you actually want the reports and evidence files I used, please just ask and I would be glad to put them up. Honestly I have never done anything with volatility up until this point and this was the first rabbit hole I really went down in the field of forensics. I have played with a lot of forensics tools by I am by no means an expert. This is also stuff from last November.
These commands are for some people who want to get started with some really awesome memory forensics.
Using Volatility 2.0 inside a Backtrack 5 Virtual machine Run by VMWare Workstation 8 I ran the following commands to obtain software information like running processes, dll, connections, and sid information and exported the information to report text files.
root@bt:~/Desktop/volatility-2.0#python vol.py psscan -f /root/Windows-XP-Professional.vmem –output-file=Report_Psscan.txt
root@bt:~/Desktop/volatility-2.0# python vol.py pslist -f /root/Windows-XP-Professional.vmem –output-file=Report_Pslist.txt
root@bt:~/Desktop/volatility-2.0# python vol.py connections -f /root/Windows-XP-Professional.vmem –output-file=Report_Connections.txt
root@bt:~/Desktop/volatility-2.0# python vol.py dlllist -f /root/Windows-XP-Professional.vmem –output-file=Report_Dlllist.txt
root@bt:~/Desktop/volatility-2.0# python vol.py getsids -f /root/Windows-XP-Professional.vmem –output-file=Report_getsids.txt
Then I used Volatility 1.3 with updated plugins and the following software in Volatility
Imaging-1.1.7
Inline-0.48_01
libdasm-1.5
Inline-Python-0.39
Pycrypo-2.0.x
Yara-1.4
Yara-python-1.4a
Pefile-1.2.10-63
volreg-0.6.tar.gz
volrip-0.1.tar.gz
by running the get_plugins.bsh script Author: Jamie Levy (gleeda)
Distorm3
Registry Ripper
root@bt:/Volatility# python volatility psscan2 -d -f /root/Windows-XP-Professional.vmem > /root/psscan2.dot
-psscan2.dot provides a processtree image in doty format to help understand running processes.
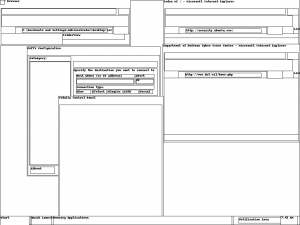
root@bt:/Volatility# python volatility screenshot -f /root/Windows-XP-Professional.vmem
Saving screenshot to 600.858ecda8.png
-screenshot plugin allows the creation of a screenshot for what the computer screen looked like at the time of the capture
python volatility hivelist -o 107563872 -f /root/Windows-XP-Professional.vmem > /203Report/Hivelist-Report.txt
– The hivelist command locates where the registry hive files reside in memory so we can run registry ripper against them.
The following commands where used to export system hive file reports with reg ripper against the provided system hive files because his program can examine registry hive files and export evidence reports into easy to read text format documents.
perl rip.pl -r /root/Windows-XP-Professional.vmem@0xe1cc2008 -f ntuser > /203Report/NTUSER-dat-01-Report.txt
perl rip.pl -r /root/Windows-XP-Professional.vmem@0xe10ea820 -f ntuser > /203Report/NTUSER-dat-02-Report.txt
perl rip.pl -r /root/Windows-XP-Professional.vmem@0xe10aab60 -f ntuser > /203Report/NTUSER-dat-03-Report.txt
perl rip.pl -r /root/Windows-XP-Professional.vmem@0xe15a3a80 -f software > /203Report/software-Report.txt
perl rip.pl -r /root/Windows-XP-Professional.vmem@0xe1580448 -f sam > /203Report/Sam-Report.txt
perl rip.pl -r /root/Windows-XP-Professional.vmem@0xe15834b8 -f security > /203Report/Security-Report.txt
perl rip.pl -r /root/Windows-XP-Professional.vmem@0xe1035b60 -f system > /203Report/System-Report.txt
root@bt:/Volatility# python volatility window_list -f /root/Windows-XP-Professional.vmem > /203Report/Windows_List-Report.txt
– The windw_list command allows us to export everything that was on the users screen at the point and time of capture of the memory image that answers the windows list question in the challenge.
I ran a lot of other stuff just looking around but this is some of the cool parts I wanted to highlight. Maybe I will put some more stuff out after I do a list of other things I want to do.
Tool Information
Cool Links to check out with more details and the real goods.
Type Name Publisher
Open Source Volatility 2.0 + Volatility 1.3 Google Code
Site: http://code.google.com/p/volatility/
Type Name Publisher
Open Source Backtrack 5 Backtrack Linux
Site: http://www.backtrack-linux.org/backtrack/backtrack-5-release/
Type Name Publisher
Commercial VMWare Workstation 8 VMware
Site: http://www.vmware.com/products/workstation/overview.html
Type Name Publisher
Open Source Imaging-1.1.7
Fredrik Lundh
Site: http://effbot.org/downloads/
Type Name Publisher
Open Source Inline-0.48_01
Brian Ingerson
Site: http://search.cpan.org/~sisyphus/Inline-0.48_01/
Type Name Publisher
Open Source Inline-Python-0.39
Ange Albertini – Google Code
Site: http://code.google.com/p/libdasm/updates/list
Type Name Publisher
Open Source Pycrypo-2.0.1
A.M. Kuchling
Site: http://www.amk.ca/python/code/crypto.html
Type Name Publisher
Commercial Yara-1.4
Google Code – Victor Manuel Alvarez
Site: http://code.google.com/p/yara-project/downloads/list
Type Name Publisher
Open Source Yara-python-1.4a
Google Code – Victor Manuel Alvarez
Site: http://code.google.com/p/yara-project/downloads/list
Type Name Publisher
Open Source Pefile-1.2.10-63
Ero Carrera
Site: http://code.google.com/p/pefile/
Type Name Publisher
Open Source volreg-0.6.tar.gz
PUSH THE RED BUTTON – MOYIX
Site: http://www.cc.gatech.edu/~brendan/volatility/
Type Name Publisher
Open Source volrip-0.1.tar.gz
PUSH THE RED BUTTON – MOYIX
Site: http://www.cc.gatech.edu/~brendan/volatility/
Type Name Publisher
Open Source Distorm3
Google Code – Gil Dabah
Site: http://code.google.com/p/distorm/
Type Name Publisher
Open Source Registry Ripper v2.02 Harlan Carvey
Site: http://regripper.wordpress.com/program-files/
Screenshot Plugin output of the challenge